Virsec Analysis of the Colonial Pipeline Attack
The Colonial Pipeline attack on Friday, May 7th, 2021 represents another in a series of advanced cyber threats, and one of the most serious incidents targeting supervisory control and data acquisition (SCADA) networks.
According to the FBI, this attack was perpetrated by Darkside, a Russian hacking group. This analysis is based on publicly available information as of May 10, 2021 and represents our estimate of techniques that were likely employed by the hackers. As events unfold and more information is available, we will continue to update our analysis.
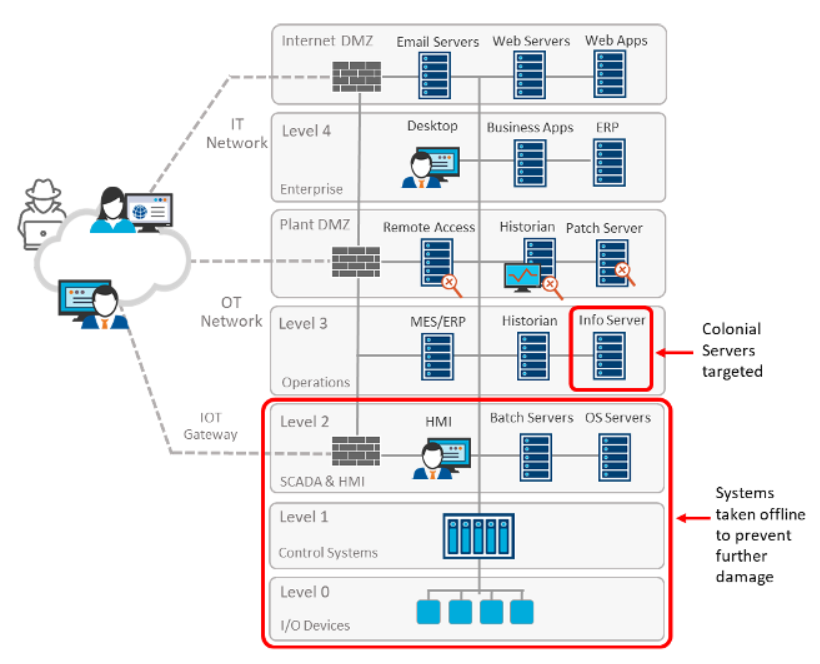
Most SCADA systems are designed with layers of separation between IT Networks (typically Internet connected) and OT Networks (more isolated).
However, as all systems are increasingly connected, these critical OT systems are accessible by IT personnel, internet-connected gateways, remote admin access, and other systems.
In the Colonial Pipeline attack, Info Servers used in the SCADA stack were infiltrated, and critical data was encrypted for ransom. Fortunately, security personnel recognized the risk and took downstream systems offline before they could be damaged by ransomware. While these actions were prudent, taking these systems offline caused significant outages for the entire pipeline system.
Attack Sequence
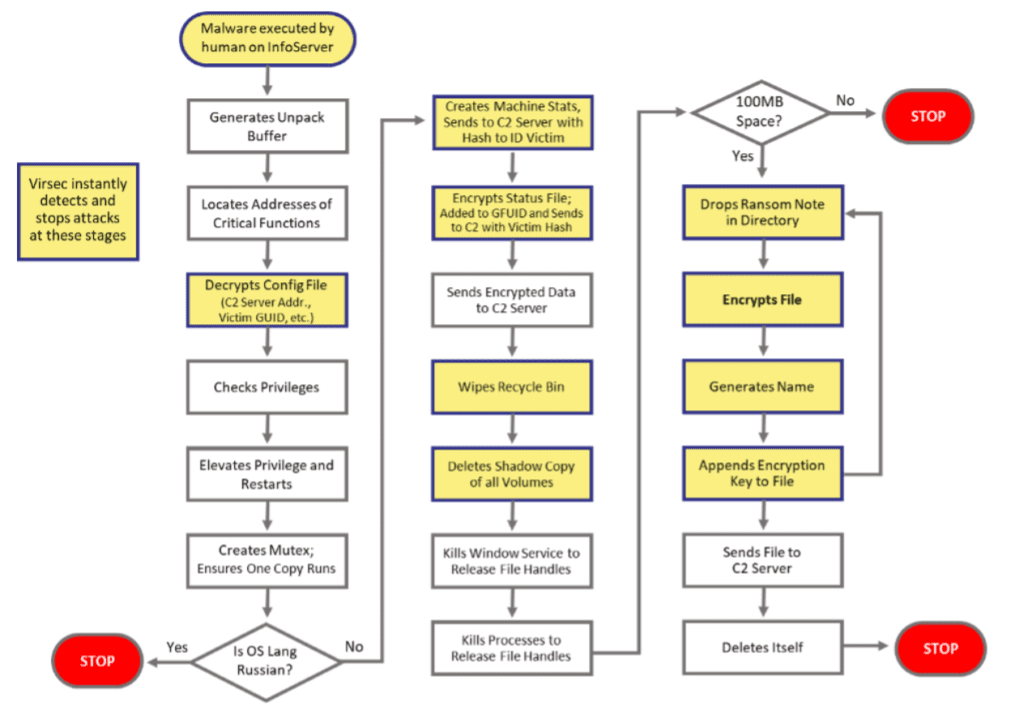
Following is a sequential breakdown of the steps that were likely used in the attack kill chain. It has not yet been disclosed how the attackers initially infiltrated the system, but there are many possible routes including spear phishing, malicious insiders, remote admin access, or exploiting other vulnerable systems.
Malware
The Darkside malware is a compressed executable, has a compressed configuration files, and leverages hybrid cryptography tools (RSA 1024 and Salsa20). The ransom note is encrypted and stored inside the compressed configuration file (that also contains a victim specific GUID and C2 server addresses).
On First Execution
Darkside generates a buffer which is used to resolve library calls and decrypted strings. It goes on to load the libraries indicated by the DLL name and finds addresses of required functions. Some of these functions are used to decrypt the configuration file. Next the malware checks if it is running with elevated privileges or not. If the user associated with the process is not an admin, it uses UAC elevation techniques to relaunch itself with higher privileges.
Next it adjusts its own token privileges and copies the security context of a logged in user. It goes onto create a unique checksum using four passes of CRC32 that will be embedded in encrypted files. It creates detailed log files to track all actions it takes. It also creates a mutex to ensure only one copy of the malware is running. Finally, also checks if the computer’s language is Russian and exits if that is the case. Darkside apparently has a policy of not attacking Russian “victims.”
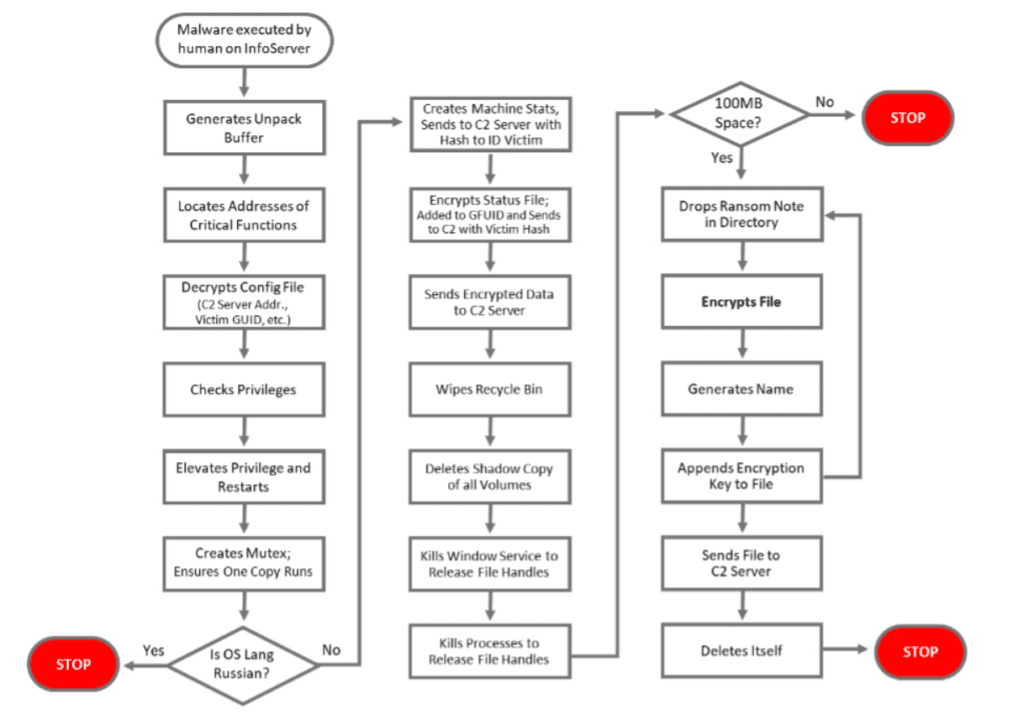
Encryption Stage
This stage starts by checking if the disk has enough storage space to put the ransom readme files in each directory. Next, the address of the C2 server to be used by this instance of Darkside is extracted from the configuration file. The malware sends the victim’s OS and other related information to the C2 server. It computes a hash with this configuration. This hash is embedded in a header in the HTTP packet which helps to identify the victim in the C2 Server.
The main attack involves wiping the Recycle Bin and deleting each volume’s copies using a PowerShell script so that the victim cannot restore the data. It also kills targeted Windows services which helps to release any file handles that are used by those services. For the same reason, it also terminates targeted processes. Next the malware recursively encrypts files until local and network shares have been encrypted. The file name, file data and the victim hash are appended to each file before it is exfiltrated to the attacker’s preferred C2 Server. As a final step, the malware deletes its own copy.
How Virsec Stops This Attack
Virsec is uniquely able to stop this type of attack during runtime, without prior knowledge of the malware or other hacking techniques used. Through its patented AppMap® technology, Virsec maps acceptable execution across the entire application stack, and instantly detects and stops any deviations during runtime. In the case of the Colonial Pipeline attack, Virsec would have detected and stopped this attack at the earliest stages of the kill chain before any damage or encryption was done. In addition, Virsec provides true application defense-in-depth and could have stopped this kill chain in at least 10 different points. The diagram below highlights the points where Virsec can stop this attack.